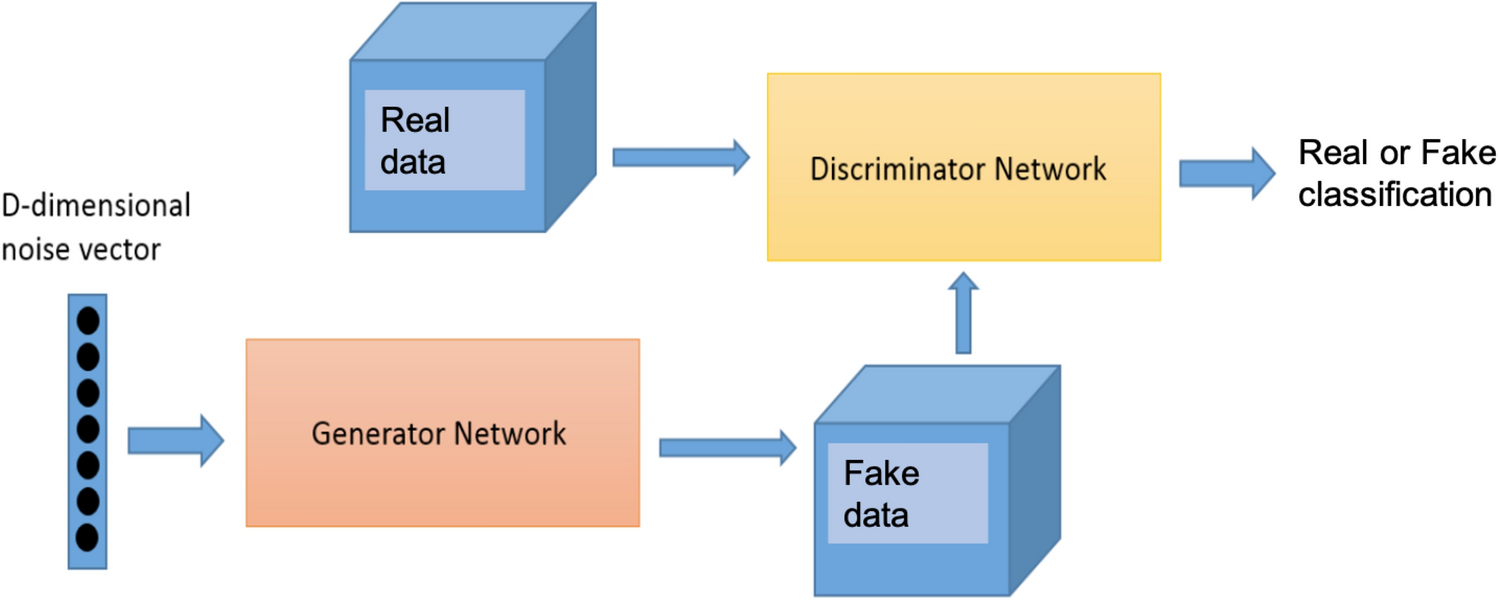
Synthetic flow-based cryptomining attack generation through Generative Adversarial Networks | Scientific Reports

How Dare They Peep into My Private Life?”: Children's Rights Violations by Governments that Endorsed Online Learning During the Covid-19 Pandemic | HRW
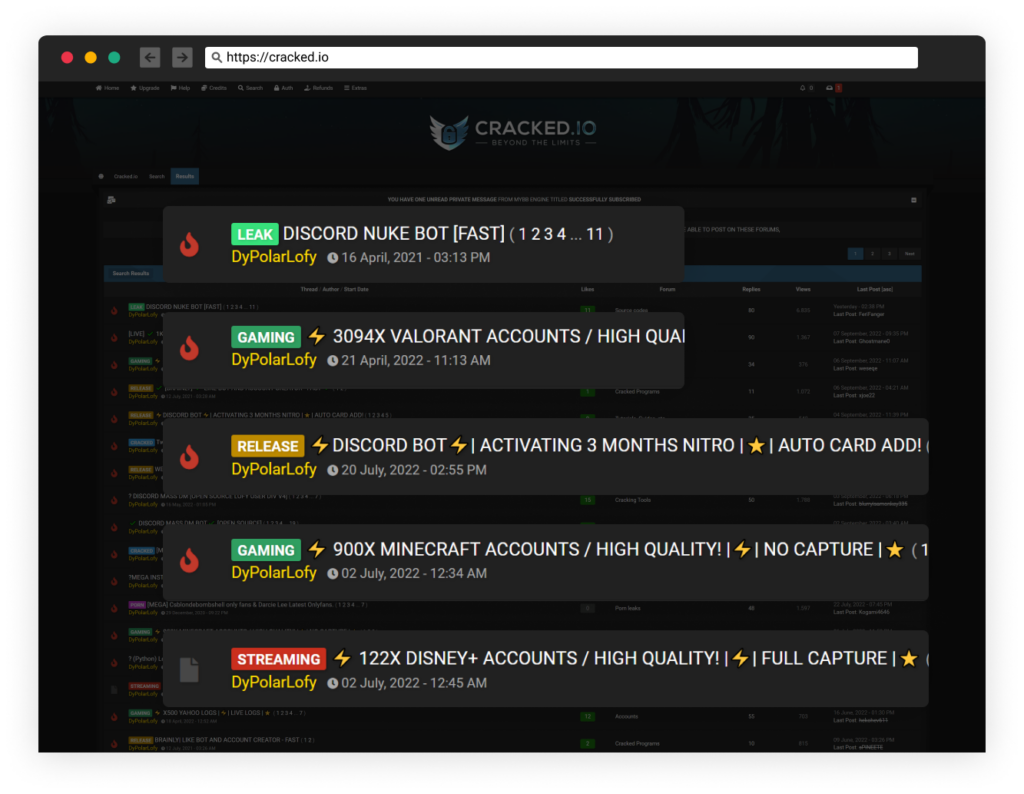
LofyGang - Software Supply Chain Attackers; Organized, Persistent, and Operating for Over a Year | Checkmarx.com
Facebook Flooded with Ads and Pages for Fake ChatGPT, Google Bard and other AI services, Tricking Users into downloading Malware - Check Point Blog